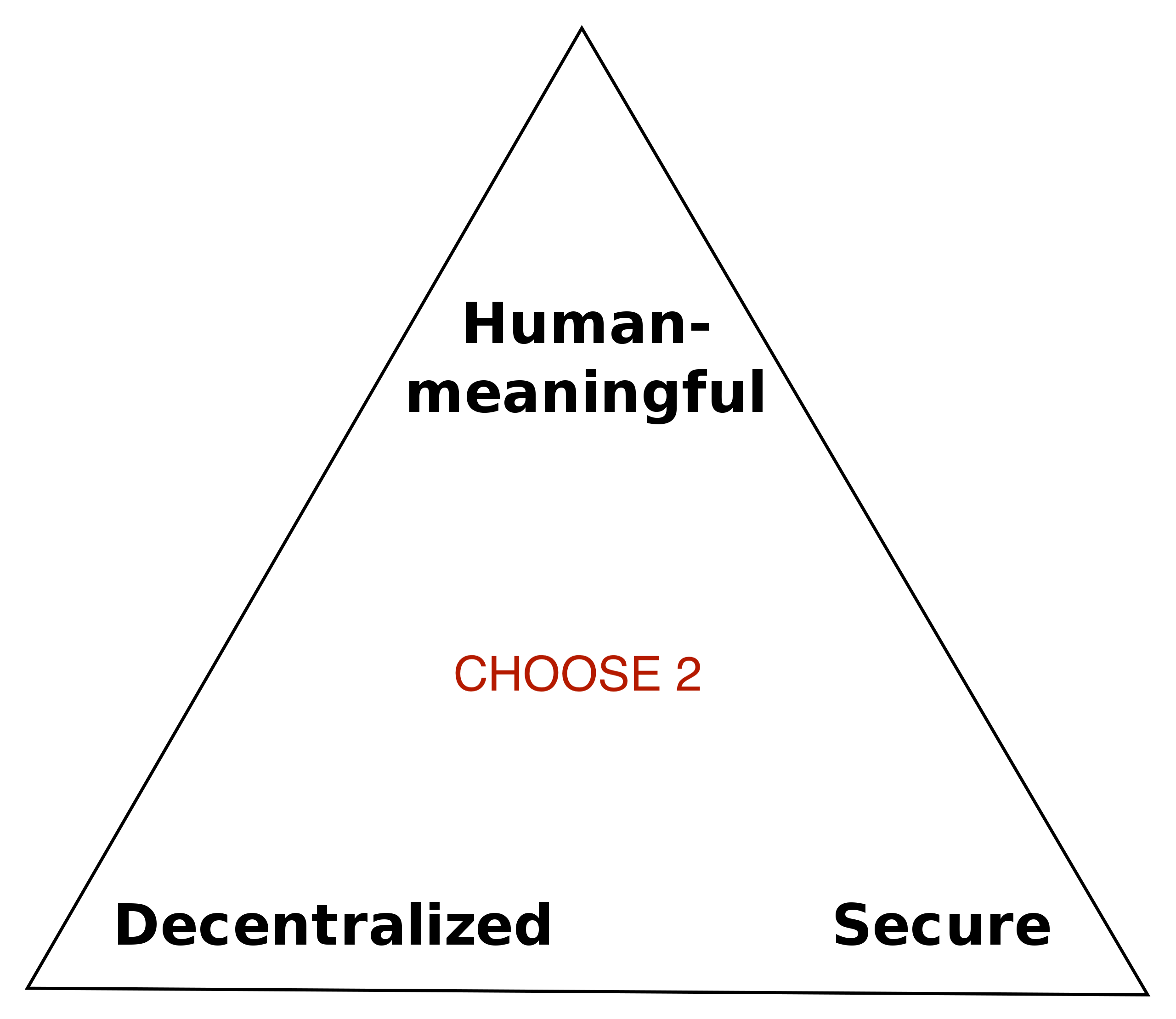
Zookos Trilemma
Zooko’s triangle states that names in a network protocol can only be one of human-meaningful or decentralized, if they wish to remain secure.
- Human Meaningful: technically this refers to names that are low entropy. But low entropy is needed to make names meaningful to humans. (eg “google.com” is low entropy)
- Decentralized: a user can resolve a name to the correct entity in the network, without asking a central trusted authority.
Examples
Human-meaningful, but not decentralized:
- DNS names
google.com - Twitter names
@thefoner - ENS names
vitalik.eth(see smart contracts decentralization)
Decentralized, but not human-meaningful:
- Tor onion addresses
mempoolhqx4isw62xs7abwphsq7ldayuidyx2v2oethdhhj6mlo2r6ad.onion - Urbit comet IDs
~doznec-salfun-naptul-habrys-doznec-salfun-naptul-habrys - Bitcoin addresses
bc1qxhmdufsvnuaeryy4ynz88fspd7xq2h9e9cetdj2h9e9cetdj
Note on brute forcing
It can be possible to make a decentralized name sort of human meaningful by using a lot of compute resources. Take for example mempool’s onion address: mempoolhqx4isw62xs7abwphsq7ldayuidyx2v2oethdhhj6mlo2r6ad.onion.
The name as a whole is not human meaningful, but the name does start with “mempool”.
Can we just brute force the whole name to be what we want? Unfortunately it’s not so simple. If the entropy in the decentralized name is low enough for users to brute force a human-meaningful name, the system will no longer be secure. To fix the security, entropy will have to be raised until no computer has the compute resources to brute-force a human meaningful name!